Configuring LDAP/AD for Ranger
Describes how to configure Ranger security so that the Ranger Admin service authenticates users through LDAP authentication, and the Ranger UserSync service sources users and groups from LDAP storage.
LDAP configuration consists of:
- Preparing the LDAP server
- Configuring the UserSync service
- Configuring the Admin service to enable LDAP
Preparing the LDAP Server
The following information about preparing the LDAP server is provided as an example. Your installation could require different procedures and steps. The following example was created with OpenLDAP running on a dedicated node installed with Ubuntu 18.04. To prepare the LDAP server, you must install the server, configure it, and provide some test data:
- Install the OpenLDAP
server:
sudo apt update && sudo apt install -y slapd ldap-utils sudo dpkg-reconfigure slapd - The terminal UI asks for some configuration information. Press
Enter in all cases except when prompted for the admin
password. When you are prompted to confirm the admin password, type
mapr. - Verify that the service is running and
responding:
$ ldapsearch -x -D 'cn=admin,dc=cluster,dc=com' -w mapr -b 'dc=cluster,dc=com' -LLL -H ldap://node2:389 dn: dc=cluster,dc=com objectClass: top objectClass: dcObject objectClass: organization o: cluster.com dc: cluster dn: cn=admin,dc=cluster,dc=com objectClass: simpleSecurityObject objectClass: organizationalRole cn: admin description: LDAP administrator userPassword:: e1NTSEF9bXVTRkNncXFEM1hIY0M1QkFiZjc2TXV1d0VYK2FjcXk= - Provide some test data. For example:
$ cat test_data.ldif dn: ou=People,dc=cluster,dc=com objectClass: organizationalUnit ou: People dn: ou=Groups,dc=cluster,dc=com objectClass: organizationalUnit ou: Groups dn: cn=ldapuser1,ou=People,dc=cluster,dc=com cn: ldapuser1 objectClass: person sn: ldapuser1 dn: cn=ldapuser2,ou=People,dc=cluster,dc=com cn: ldapuser2 objectClass: person sn: ldapuser2 dn: cn=ldapuser3,ou=People,dc=cluster,dc=com cn: ldapuser3 objectClass: person sn: ldapuser3 dn: cn=ldapuser4,ou=People,dc=cluster,dc=com cn: ldapuser4 objectClass: person sn: ldapuser4 dn: cn=ldapgroupA,ou=Groups,dc=cluster,dc=com objectClass: groupOfNames member: cn=ldapuser1,ou=People,dc=cluster,dc=com member: cn=ldapuser2,ou=People,dc=cluster,dc=com cn: ldapgroupA dn: cn=ldapgroupB,ou=Groups,dc=cluster,dc=com objectClass: groupOfNames member: cn=ldapuser3,ou=People,dc=cluster,dc=com member: cn=ldapuser4,ou=People,dc=cluster,dc=com cn: ldapgroupB $ ldapadd -x -D 'cn=admin,dc=cluster,dc=com' -w mapr -H ldap://node2:389 -f test_data.ldif adding new entry "ou=People,dc=cluster,dc=com" adding new entry "ou=Groups,dc=cluster,dc=com" adding new entry "cn=ldapuser1,ou=People,dc=cluster,dc=com" adding new entry "cn=ldapuser2,ou=People,dc=cluster,dc=com" adding new entry "cn=ldapuser3,ou=People,dc=cluster,dc=com" adding new entry "cn=ldapuser4,ou=People,dc=cluster,dc=com" adding new entry "cn=ldapgroupA,ou=Groups,dc=cluster,dc=com" adding new entry "cn=ldapgroupB,ou=Groups,dc=cluster,dc=com" - Specify user passwords, and verify LDAP
authentication:
$ for i in $(seq 4) ; do ldappasswd -D 'cn=admin,dc=cluster,dc=com' -w mapr -x "cn=ldapuser${i},ou=People,dc=cluster,dc=com" -s "pass${i}" -H ldap://node2:389 ; done $ for i in $(seq 4) ; do ldapwhoami -x -D "cn=ldapuser${i},ou=People,dc=cluster,dc=com" -w "pass${i}" -H ldap://node2:389 ; done dn:cn=ldapuser1,ou=People,dc=cluster,dc=com dn:cn=ldapuser2,ou=People,dc=cluster,dc=com dn:cn=ldapuser3,ou=People,dc=cluster,dc=com dn:cn=ldapuser4,ou=People,dc=cluster,dc=com - Run
ldapsearchagain to check if everything is okay. The result should look like this:$ ldapsearch -x -D 'cn=admin,dc=cluster,dc=com' -w mapr -b 'dc=cluster,dc=com' -LLL -H ldap://node2:389 dn: dc=cluster,dc=com objectClass: top objectClass: dcObject objectClass: organization o: cluster.com dc: cluster dn: cn=admin,dc=cluster,dc=com objectClass: simpleSecurityObject objectClass: organizationalRole cn: admin description: LDAP administrator userPassword:: e1NTSEF9bXVTRkNncXFEM1hIY0M1QkFiZjc2TXV1d0VYK2FjcXk= dn: ou=People,dc=cluster,dc=com objectClass: organizationalUnit ou: People dn: ou=Groups,dc=cluster,dc=com objectClass: organizationalUnit ou: Groups dn: cn=ldapuser1,ou=People,dc=cluster,dc=com cn:: bGRhcHVzZXIxIA== objectClass: person sn: ldapuser1 userPassword:: e1NTSEF9eUVKaU1SYU5ub3AxeWxjVXk5aDVuNGJuYldmMVdHSDk= dn: cn=ldapuser2,ou=People,dc=cluster,dc=com cn:: bGRhcHVzZXIyIA== objectClass: person sn: ldapuser2 userPassword:: e1NTSEF9NmtLSHFXeUVwTTBtNHVBQjU3TGZueGduN3VaSXovWlc= dn: cn=ldapuser3,ou=People,dc=cluster,dc=com cn:: bGRhcHVzZXIzIA== objectClass: person sn: ldapuser3 userPassword:: e1NTSEF9UWVyeVZFVW9EMWpGdUpBZng4NVBQNmVKTzVsbjhWWEM= dn: cn=ldapuser4,ou=People,dc=cluster,dc=com cn:: bGRhcHVzZXI0IA== objectClass: person sn: ldapuser4 userPassword:: e1NTSEF9cy9xdm82RGh3Z2RjamZRbGZSZmdMTW03QjRCajJtdmM= dn: cn=ldapgroupA,ou=Groups,dc=cluster,dc=com objectClass: groupOfNames member: cn=ldapuser1,ou=People,dc=cluster,dc=com member: cn=ldapuser2,ou=People,dc=cluster,dc=com cn: ldapgroupA dn: cn=ldapgroupB,ou=Groups,dc=cluster,dc=com objectClass: groupOfNames member: cn=ldapuser3,ou=People,dc=cluster,dc=com member: cn=ldapuser4,ou=People,dc=cluster,dc=com cn: ldapgroupB
Configuring the UserSync Service
The UserSync service can source users and groups from the LDAP server and push them to
the Ranger Admin service. To configure this functionality:
- Specify the following properties in the UserSync
install.propertiesfile:SYNC_SOURCE = ldap SYNC_LDAP_URL = ldap://node2:389 SYNC_LDAP_BIND_DN = cn=admin,dc=cluster,dc=com SYNC_LDAP_BIND_PASSWORD = mapr SYNC_LDAP_SEARCH_BASE = dc=cluster,dc=com SYNC_GROUP_SEARCH_ENABLED=true SYNC_GROUP_USER_MAP_SYNC_ENABLED=true - Run the UserSync
setup.shscript, and restartranger-usersync. You should see the following users in the admin users tab:
You should see the following groups in the groups tab: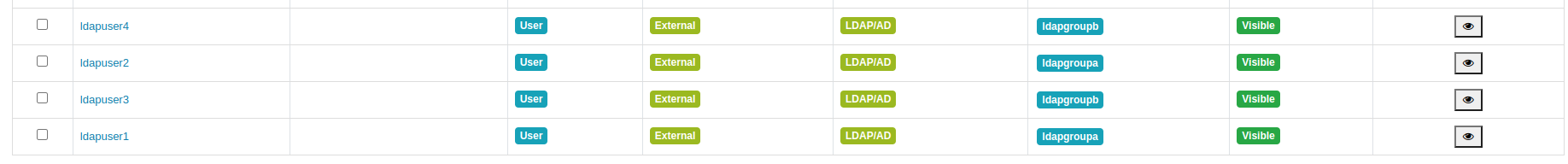

Configuring the Admin Service
The Admin service authenticates users when logging into the web UI through LDAP
authentication. To configure this functionality:
- Specify the following properties in the Admin
install.propertiesfile:authentication_method=LDAP xa_ldap_url=ldap://node2:389 xa_ldap_userDNpattern=cn={0},ou=People,dc=cluster,dc=com xa_ldap_groupSearchBase=dc=cluster,dc=com xa_ldap_base_dn=dc=cluster,dc=com xa_ldap_bind_dn=cn=admin,dc=cluster,dc=com xa_ldap_bind_password=mapr - Run the Admin service
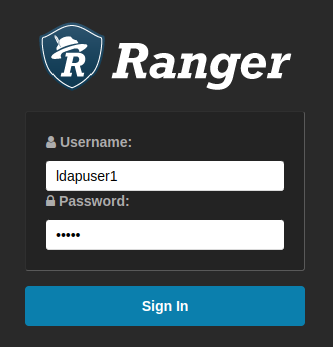
setup.shscript, and restart the service. After restarting the service, you should be able to log in to the web UI by usingldapuser1and passwordpass1: