Stream Security
The adminperm, copyperm, comsumeperm, produceperm, and topicperm security permissions protect topics in a stream from unauthorized access. In addition, data-fabric supports user impersonation.
ACE Permissions
The following Access Control Expression (ACE)s are used to protect topics in a stream from unauthorized access. ACEs are set when you create or edit a stream.
adminperm- Determines which users can modify ACEs for a stream, set up replication of a stream, and modify other attributes of a stream. By default, the stream owner and the Data Fabric user can modify this setting.
copyperm- Determines the users who can run the
mapr copystreamandmapr diffstreamsutilities on the stream. consumeperm- Determines the users who can read messages in topics from a stream.
produceperm- Determines the users who can publish messages to topics in a stream.
topicperm- Determines the users who can create topics in a stream or remove them.
The following example shows the adminperm, consumeperm,
produceperm, and topicperm permissions on a stream named
traffic_sensors, which includes the topics
traffic_sensors_sf and traffic_sensors_ny.
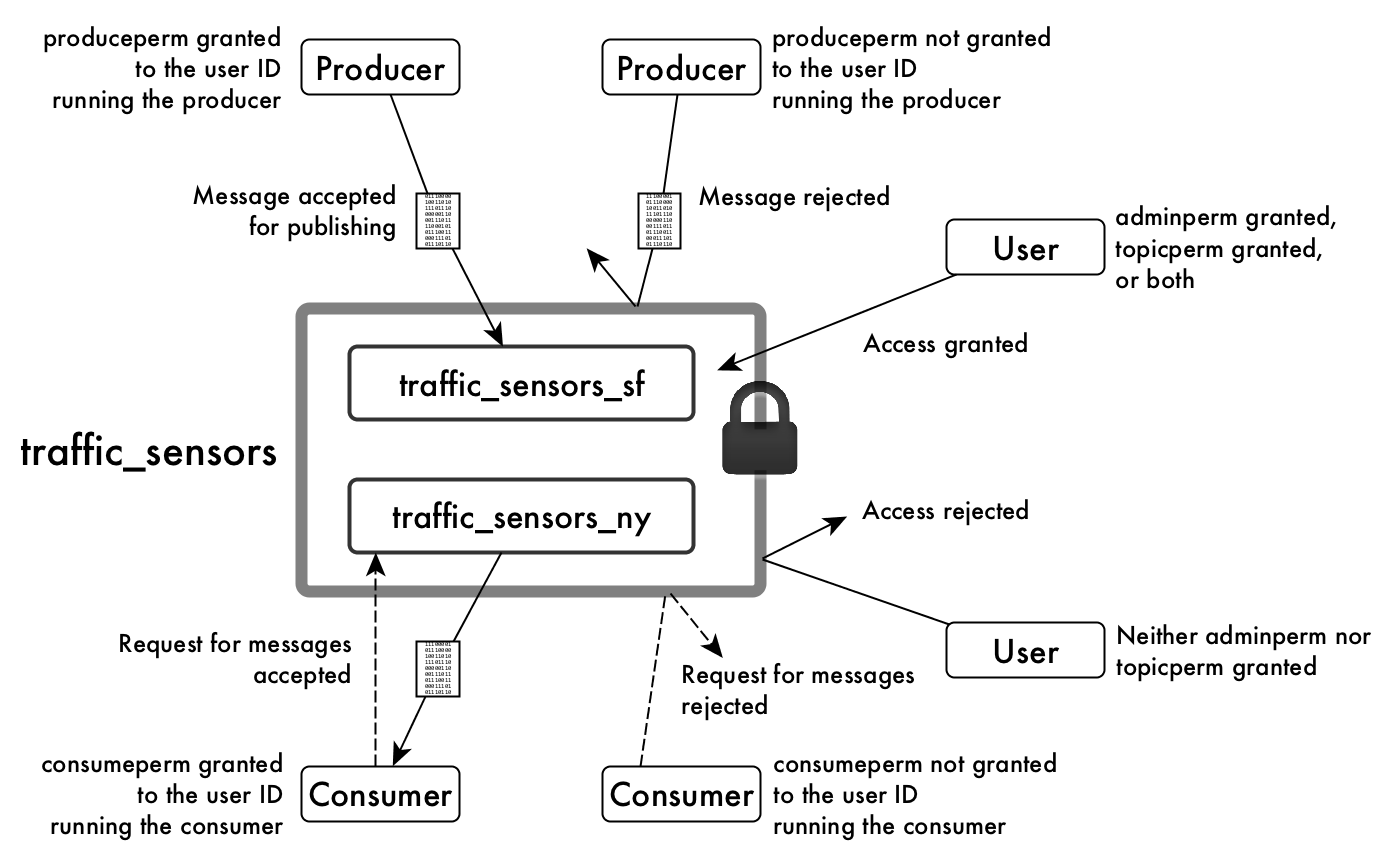
For general information about ACEs, see ACE Syntax.
User Impersonation
HPE Ezmeral Data Fabric Streams supports user impersonation through the Java API. See HPE Ezmeral Data Fabric Streams Java API Library for more information. HPE Ezmeral Data Fabric Streams does not support user impersonation through the C API or Python API.
Kafka REST supports outbound user impersonation. See User Impersonation for more information.