Changing the State of a Security Policy
The security policy state indicates whether users can apply a security policy to data
objects and whether the system enforces the ACEs set in the security policy. An administrator
can change the state of a security policy through the allowtagging and
accesscontrol parameters when creating or modifying a security policy from
the maprcli or equivalent REST API comands.
The following table describes the
allowtagging and
accesscontrol parameters. | Parameter | Default | Accepted Values and Descriptions |
|---|---|---|
| allowtagging | false |
false
true
|
| accesscontrol | Disarmed |
Disarmed
Armed
Denied
|
Changing the State of a Security Policy
An administrator can change the state of a security policy through the
allowtagging and accesscontrol parameters to move a
security policy through a life cycle, as shown in the following image where the security
policy moves from new to retired.
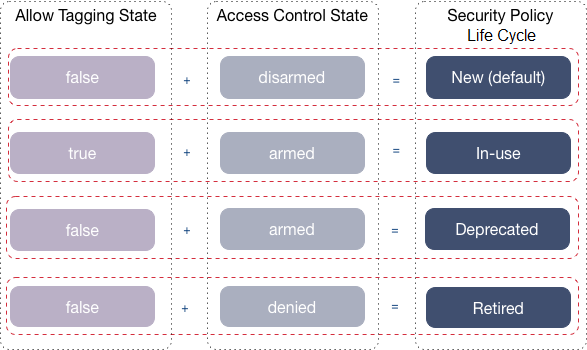
The following table describes each of the stages in the security policy life cycle:
| Stage | Description |
|---|---|
| New (default) |
|
| In-use |
|
| Deprecated |
|
| Retired |
|