HSM Functionality Description
Describes how KMIP Keystores work.
HSM integration with data-fabric works as follows:
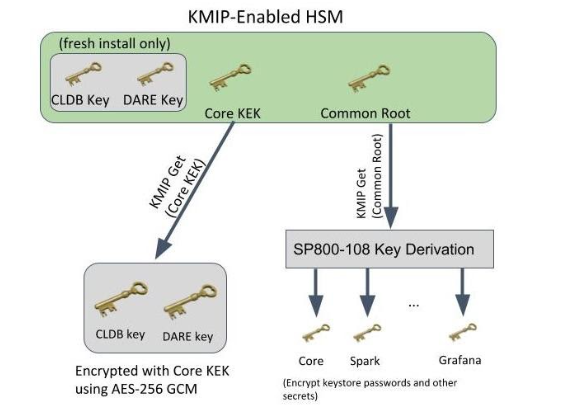
- If the external HSM functionality is enabled and there is an active connection to the external key store, the CLDB and DARE master keys are encrypted with the data-fabric Core Key Encryption Key (KEK) that is stored in the external key store.
- For fresh installations, the CLDB and DARE master keys are generated in the external key
store, and remain in the external key store for backup purposes. The CLDB and DARE keys
are stored in the
${MAPR_HOME/conf/tokens/mrhsm.confconfiguration file, encrypted with the data-fabric Core KEK. - For existing installations that already have the CLDB and DARE keys generated, the existing keys remain, but are stored in an encrypted format, encrypted with the Core KEK.
- Installations upgrading from an existing data-fabric release will also have its CLDB and DARE keys stored in the external HSM for disaster recovery purposes.
- Re-keying of the Core or Common KEK is supported. Re-keying the Core KEK requires re-encrypting the CLDB and DARE master keys using the new Core KEK.
IMPORTANT The SP800-108 key derivation is not supported for the data-fabric 6.2 release.
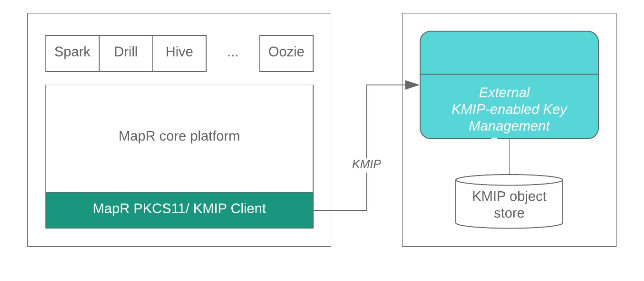
The data-fabric core platform contains the external HSM integration functionality. You can
access the HSM using the industry standard PKCS#11 API and KMIP, which provide enhanced
security for enterprise grade applications to protect data-at-rest. This access is transparent
both to the data-fabric core functionality and to ecosystem components such as Spark, Drill
and Hive after you set up the KMIP integration to the data-fabric core platform using the
mrhsm Commands, as illustrated in the following diagram:

Setting Up HSM
To setup HSM, see Setting Up the External KMIP Keystore.