Security
Provides an overview of the MapR security features.
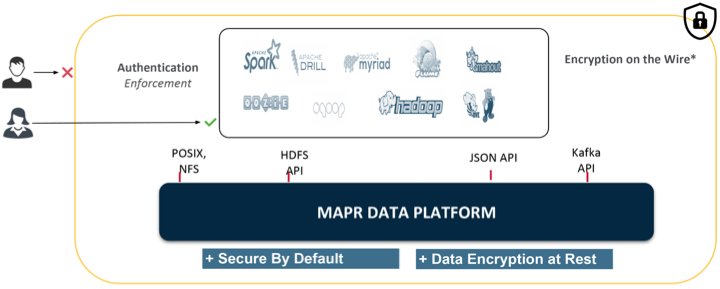
Securing enterprise data is critical. To make securing data in clusters easy, the MapR Data Platform has a data protection scheme built directly into the platform that is enabled by default, simplifying the process of protecting critical data. You can take advantage of the default security settings, or you can implement data security manually. Either way, it is important to identify which data to secure.
Since data must be shared between nodes on the cluster, data transmissions between nodes, and from the cluster to the client are vulnerable to interception. Networked computers are also vulnerable to attacks where an intruder successfully pretends to be another authorized user and then acts improperly as that user. Additionally, networked machines share the security vulnerabilities of a single node. The MapR Data Platform supports the ability to apply protection directly as data enters and exits the platform. You do not need to apply an external management server or particular security plugin.
- Secure by Default
-
MapR, which includes the MapR Data Platform and EEP components, is secure out-of-the-box on all new installations, ensuring all network connections require authentication and all data in motion is protected with wire-level encryption. MapR provides the ability to apply security protection directly for data as it comes into and out of the platform without requiring an external security manager server or a particular security plugin for each ecosystem component. The security semantics are applied automatically on data being retrieved or stored by any ecosystem component, application, or users.
- Platform-Based Security
-
The MapR Data Platform applies security semantics automatically as data is being stored and retrieved from the platform. It supports all four pillars of security (authentication, authorization, auditing, and encryption), using platform-level capabilities that do not require external security tools or plugins.
- Encryption
The following sections describe the MapR security capabilities and security architecture.
Security Capabilities
A secure MapR environment is predicated on authentication, authorization, auditing, and encryption capabilities. You can use policy-based security to classify and manage these capabilities.
- Authentication
-
Restricting access to a specified set of users.
Robust authentication prevents third parties from representing themselves as legitimate users. MapR supports a wide range of authentication mechanisms depending on the network transport. These mechanisms include MapR tickets, Kerberos, Pluggable Access Module (PAM), Basic Authentication, MapR-SASL, and SPNEGO.
See Configuring Authentication for more information.
- Authorization
-
Restricting an authenticated user's capabilities on the system.
MapR provides sophisticated authorization controls to ensure that users can perform only the activities for which they have permissions, such as data access, job submission, cluster administration, and more. These permissions can be granted by an administrator through the browser-based Control System management and monitoring interface, or by using the command-line utilities.
See Managing Access Controls for more information.
- Auditing
-
Logging audit records of operations.
MapR allows you to log audit records of cluster-administration operations and operations on directories, files, and tables.
See Managing Auditing for more information.
- Encryption
-
Restricting an external party's ability to read data.
Encryption is used to avoid exposure to breaches, such as packet sniffing and theft of storage devices. In a secure MapR cluster, data transmission between nodes, and between a MapR cluster and ecosystem application is encrypted, preventing an attacker with access to that communication from gaining information about the contents of the transmission. Optionally, you can enable encryption for data at rest to prevent unauthorized users from accessing sensitive data, and protect against data theft through sector-level disk access.
Data is protected by encrypting all data being transmitted over the wire and optionally encrypting all that is stored on the MapR platform. The MapR data encryption scheme is built directly into the platform and is enabled by default.
See Managing Encryption for MapR Core for more information.
Security Architecture
MapR provides the following authentication and authorization functionality:
- File System Permissions
- For files and directories on the MapR cluster, you can leverage standard Unix-style permissions to grant access to authorized users. Since MapR File System is a POSIX-like file system, you can set user permissions as you would on any other Linux system. See Setting MapR File System Permissions for more information.
- Cluster, Volume, and Job Queue Access Control Lists (ACLs)
- You can specify the actions that a given user can perform on each of these cluster elements. You can use access control lists (ACLs) to grant permissions for performing administrative tasks at both the cluster and the volume level. See Managing Access Control Lists for more information.
- Access Control Expressions for File System and Natively Stored MapR Database Tables
- ACEs control which files, directories, volumes, streams, and tables users or groups can access. ACEs are a powerful and flexible mechanism to grant permissions on structured and unstructured data. See Managing Access Control Expressions for more information.
- Impersonation for Centralized Control of Access to Resources
-
Impersonation, also known as identity assertion, is one user accessing data and submitting jobs on behalf of another user. See Managing Impersonation for more information.
What to do Next
The secure-by-default data platform provides security through a single option in the MapR Installer or by running the configure.sh script with the
-secure option after a manual installation. You can enable security on
your cluster using the procedure described in the following topics:
- Using the Enable MapR Secure Cluster Option if you are installing with the MapR Installer.
- Enabling Security if you are Installing without the MapR Installer.
After enabling security, optionally, you can perform the following tasks:
- Understand the security exceptions and take corrective action, where applicable.
- Configure authorization on the resources.
- Configure auditing on administration and resources.
- Configure encryption for data at rest.
- If you have Hive installed, enable storage-based authorization for the Hive Metastore server.